Juniper - OSPF Configuration Part - IV
이번에는 JunOS 의 기본 System 설정을 다뤄 볼까 합니다.
System 설정이 뭔데? 라고 하시는 분이 계실 듯하여 간단히 언급하자면~
Name Server, NTP, Syslog, SNMP등 장비 운영에 필요한 설정들을 대상으로 합니다 :)
일단 기존에 쓰던 Lab에 추가로 위와 같이 VMware Workstaion, Virtual Box, 혹은 vSphere(ESXi) 등과 연결할 수 있도록
Cloud Interface를 추가 했습니다.
그리고 JunOS-3 라우터에서 Default Route를 OSPF로 전파~
마지막에 Virtual-Link설정을 한 JunOS-6에서 Google DNS서버인 8.8.8.8까지 통신이 되는걸 확인할 수 있습니다.
이제 필요한 듯, 필요 없는 Name Server 등록부터 해볼까 합니다.
IP 기반의 운영에 익숙하신 분들은 IP를 외우고 있는데 왜 NS등록까지 하지? 하고 하실 수 있으나 장비의 수량이 많아지고, IPv6기반으로 넘어가게 되거나 국내뿐 아니라 글로벌 인프라를 운영하게 되면 NS를 이용하는 것이 매우 편합니다 :)
하여 제 랩에 있는 Windows Domain Name Server에 연결해볼까 합니다. :)
How to configure the DNS server:
1. Begin by including the IP address(es) of your DNS server(s) within a
name-server statement(s):
set system name-server 172.26.27.2
set system name-server 172.26.27.3
2. It’s good practice to configure the domain name in which the device
itself is located. JUNOS then uses this configured domain name as the
default domain name to append to hostnames that are not fully
qualified:
set system domain-name enterprise.com
3. If your device can reach several different domains, you can configure
these as a list of domains to be searched. JUNOS then uses this list to
set an order in which it appends domain names when searching for the
IP address of a host.
set system domain-search [enterprise.com department.enterprise.com]
This command example configures JUNOS to search the enterprise.
com and then the department.enterprise.com domains when
attempting to resolve unqualified hosts
위 내용을 토대로 설정해 보겠습니다.
설정 후 NS query 가 잘 동작하는 모습입니다 :) 오예~
이제 NTP를 연동해 보겠습니다.
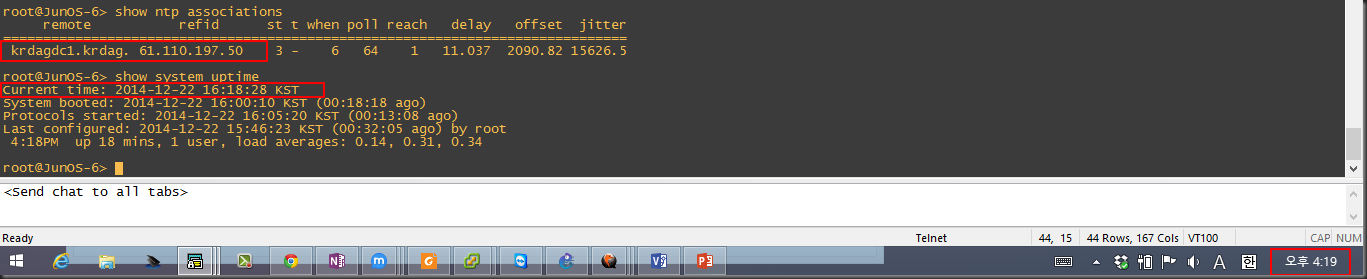
우선 잘은 안보이지만; 현재 시스템의 시간을 확인합니다.
역시 현재 시간과 1시간정도의 차이가 있습니다.
How to use a remote time server:
In large networks it’s useful to have an NTP server to set the exact same
time across all the network devices. The common reference lets you
correlate all timestamps of logs and trace files for troubleshooting
purposes.
Use the following steps to configure your device to use one or more NTP
servers.
20 Day One: Configuring JUNOS Basics
1. The easiest way to have NTP set the time is to have JUNOS retrieve the
time when it first boots up. Use the following command with the IP
address of your NTP server:
set system ntp boot-server 172.26.27.4
2. To keep the device synchronized with periodic updates, configure a
reference NTP server (you can configure more than one). It’s good practice
to do this, as the JUNOS device can be up for a long time, and therefore
the clock can drift:
set system ntp server 172.26.27.4
3. Next, you may want set the local time zone to match the device’s
location (note that Universal Coordinated Time (UTC) is the default). This
allows JUNOS to present the time in the correct local format, accounting
for things such as offset from UTC, which may change several times
throughout the year:
set system time-zone Europe/Amsterdam
TIP Many administrators prefer to keep all their devices configured to use the
UTC time zone. This approach has the benefit of allowing you to easily
compare the time stamps of logs and other events across a network of
devices in many different time zones.
4. If you’ve just booted JUNOS and need to synchronize time with a
remote time source, you can do so in operational mode:
root@juniper1> set date ntp 172.26.27.4
7 Apr 10:32:27 ntpdate[4544]: step time server 172.26.27.4 offset -0.000565 sec
위와 같이 설정을 하면, 짜잔~
역시 잘은 안보이지만 ㅎㅎ 약 1분정도의 오차가 있지만 시간이 맞아 졌습니다 :)
NTP를 사용하는 이유는 아시겠지만 장애처리 Event log확인 등을 할 때 하나의 장비 뿐아니라 여러 장비의 Log를 함께 봐야하는데 이 떄 각각의 장비의 Time Stamp가 다르면 매우 곤란합니다. 이를 방지 하기 위해 어느정도 규모의 인프라라면 당연히!! 설정하셔야 합니다 :)
Login Banner 설정.
저희 나라뿐 아니라 여러 나라에서 운영장비에 대한 보안 감사 시 꼭! 들어있는 항목이죠.
접근 제한과 Login Banner 행여라도 열려있는 Terminal Port로 비 인가자가 접근했을 때, 겁주는 용이죠 ㅎㅎ 경고!!
Login Message
A login message displays a banner to all users when they access the
device, before they log in. The message can be split over multiple lines
by using \n (newline, equivalent to a carriage return and line feed) as a
delimiter:
set system login message “ Welcome \n to \n JUNOS Training\n “
After you set up the message above, any user accessing your device sees
it displayed on their screen. For example, if the remote client is using the
Secure Shell (SSH):
$ ssh juniper1
Welcome
to
JUNOS Training
root@juniper1’s password:
TIP Use the login message to warn others that unauthorized access to your
device is prohibited (ask your legal department for the preferred statement in your organization):
set system login message “WARNING: Unauthorized access is an
offense”
이렇게 위와 같이 자신의 문구를 "" 안에 적어서 설정하면~ 아래와 같이 경고를 날릴 수 있습니다.
아.... 덤으로 Remote Access (Telnet, SSH등)은 아래와 같이 설정하면 된다.
Enabling Remote Access
SSH, telnet, and FTP are widely-used standards for remotely logging into
network devices and exchanging files between systems. Before authorized users can access your device, or your device can exchange data with
other systems, you must configure one or more of these enabling services.
They are all disabled by default in JUNOS.
SSH is telnet’s successor and is the recommended method for remote
access. SSH encrypts all traffic, including passwords, to effectively
eliminate eavesdropping, connection hijacking, and other attacks. The
SSH utility includes SCP (secure copy), a file transfer program that uses
SSH and is the recommended method for secure file exchange.
Use the following commands to set up the services that are needed in
your device:
set system services ftp
set system services telnet
set system services ssh
이제는 장비 모니터링을 위한 필수 요소 SNMP 설정이다.
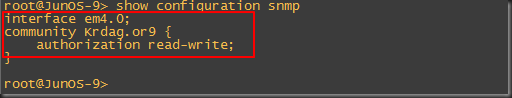
How to create a read-only SNMP community:
1. Refer to what you recorded in Chapter 1 as the community string of
the SNMP community used in your network. This example uses the de
facto standard name public to create a community that gives limited
read-only access:
[edit groups common]
jadmin@juniper1# set snmp community public
36 Day One: Configuring JUNOS Basics
2. Now focus your configuration statements onto this new branch of
the configuration hierarchy:
edit snmp community public
3. Define the authorization level for the community:
[edit groups common snmp community public]
set authorization read-only
In the above command you are confining the public community to
read-only access. Now any SNMP client (for example, an SNMP
management system) that belongs to the public community can read
MIB variables but cannot set (change) them.
4. Define a list of clients in the public community who are authorized
to communicate with the SNMP agent in JUNOS. List the clients by IP
address and prefix. Typically the list includes the SNMP network
management system in your network, or the address of your
management network. The following statement defines the network
192.168.1.0 (and any host within it) as being authorized:
set clients 192.168.1.0/24
5. Define the clients that are not authorized within the public
community by specifying their IP address, followed by the restrict
statement:
set clients 0.0.0.0/0 restrict
읽어 보면 대충 감이 오시겠지만 Cisco IOS와 거의 비슷하다.
바로 실습 들어갑니당 :)
설정을 간단하게 하고 동작하는지 확인하면 됩니다 :)
SNMP의 경우 장비 자체 에서 확인하는 건 "show snmp statistics" 로 snmp packet이 들어왔나, 응답했나 정도라서
가능하면 설정 후 실제로 테스트를 해보는 게 가장 좋습니다 :)
NMS가 있다면 등록해보시면 좋고 없다면 아래와 같이 SNMP Tester를 사용하시면 좋습니다.
두 가지 다 해보도록 하죠 :)
우선 Tester는 아래 URL에서 무료로 구하실 수 있습니다
http://download-cdn.paessler.com/download/snmptester_5_1_3.zip
받아서 압출을 풀어보면~
위와 같은 파일들이 확인되고 실행해 봅니다 :)
실행을 하고 위에 표시된 부분을 입력하고 Start하시면 :)
장비에서는 이렇게 Packet in/out이 확인되고
Tester에서는 아래와 같이 해당 정보를 가져오게 됩니다 :)
Test 중인 PaaS NMS인 Auvik에서도 시간은 좀 걸리지만 위에 그림처럼 하나씩 긁어오네요 :) ㅎㅎ
이번 포스팅은 여기까지 하고 다음에는 인증서버와 연동을 해볼까 합니다 :)
수고하셨습니다.




![clip_image005[1] clip_image005[1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiHcrNoqVlG3Z4-G5p2hEsfkl_5y4VT2uzZE_pAoJYHKHh6qw3IR2VD-aL9CKKxITLRdck33hKXKLMgXcJLMbfGGPCat7f7BoMCUoEy394Eza5R5RbcrVLZ-iEj8OZUuzFvr5CPKuMH418/?imgmax=800)








Fortunes Online - Play Casino Games - FABCASINO.COM
답글삭제Play online 바카라 casino games for real money. งานออนไลน์ Best Fortunes Online Slots 2021. Play slots online, poker, roulette, blackjack, kadangpintar
Juniper - Ospf Configuration Part - Iv >>>>> Download Now
답글삭제>>>>> Download Full
Juniper - Ospf Configuration Part - Iv >>>>> Download LINK
>>>>> Download Now
Juniper - Ospf Configuration Part - Iv >>>>> Download Full
>>>>> Download LINK EF